Security
Cloud Security
Cloud security is a critical aspect of cloud computing that involves protecting cloud-based systems, applications, and data from unauthorized access, modification, or destruction. It encompasses a wide range of security measures and practices that are designed to safeguard sensitive information and ensure the integrity and availability of cloud-based resources.
Key Concepts
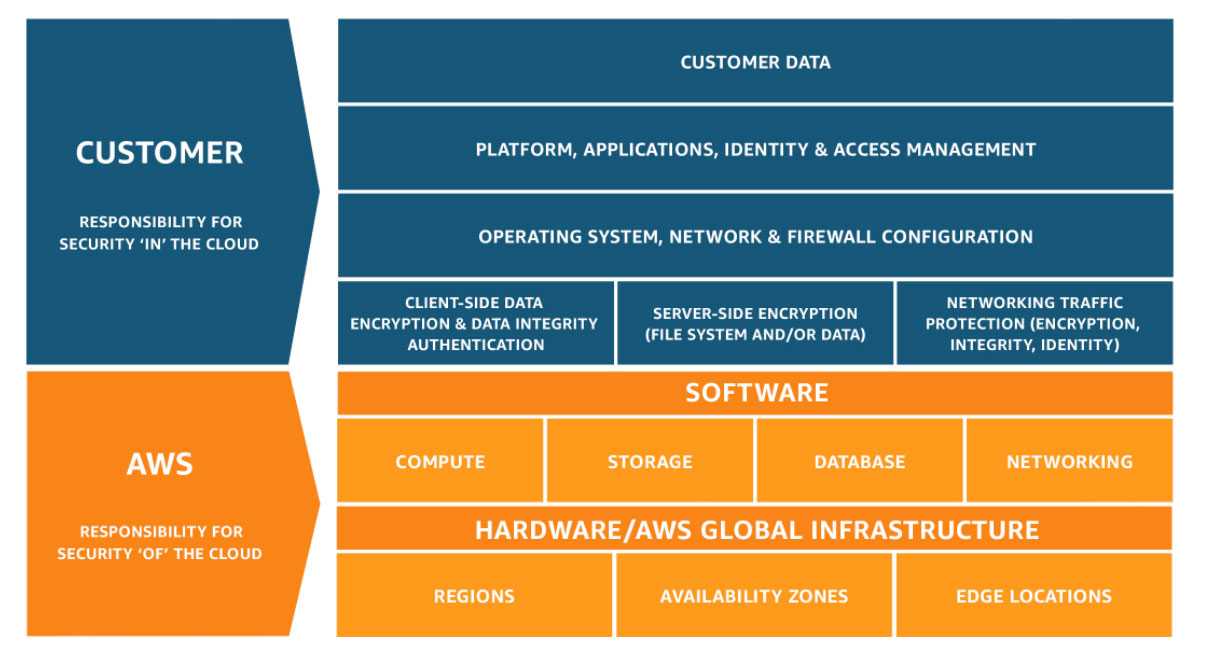
- Shared Responsibility Model: Cloud security is a shared responsibility between cloud providers and cloud customers. Cloud providers are responsible for securing the infrastructure, while cloud customers are responsible for securing their workloads and data within the cloud environment.
- Threats and Vulnerabilities: Cloud environments are susceptible to various threats, including cyberattacks, data breaches, insider threats, and misconfigurations. Vulnerabilities in software, systems, and configurations can be exploited by attackers to gain unauthorized access or disrupt operations.
IAM
Identity and Access Management (IAM) is a web service that helps you securely manage access to AWS resources. IAM enables you to create and control users, groups, and roles that define who can access what within your AWS account.
Key Components of IAM are,
Users: Represent individual people who can access AWS resources. Each user has a unique name and a set of credentials, such as an access key ID and a secret access key.
Groups: Collections of users who share common permissions. Groups can be used to manage permissions for multiple users at once.
Roles: Entities that can be granted permissions to access AWS resources. Roles are often used to grant temporary access to resources, such as when launching EC2 instances.
Policies: Documents that define permissions for users, groups, and roles. Policies specify which actions users can perform on which resources.
5 Steps to securing your Cloud
Step 1: Implement Identity and Access Management (IAM)
Enable IAM Roles: Use IAM roles to grant temporary access permissions to resources instead of long-term access keys. This reduces the risk of credential exposure and unauthorized access.
Enforce Multi-Factor Authentication (MFA): Mandate MFA for all IAM users to add an extra layer of security beyond passwords. This can significantly reduce the chances of unauthorized access even if passwords are compromised.
Manage IAM User Permissions: Regularly review and update IAM user permissions to ensure they align with their roles and responsibilities. Avoid granting excessive permissions that could lead to accidental or malicious actions.
Principle of Least Privilege: Apply the principle of least privilege, granting users only the minimum permissions necessary for their tasks. This minimizes the potential damage if an account is compromised.
Step 2: Secure Your Storage
Encrypt Data at Rest and in Transit: Encrypt your data at rest (stored in S3 buckets, EBS volumes, etc.) and in transit (when moving between resources) using industry-standard encryption methods like AES-256.
Enable Access Controls for Storage Resources: Implement access controls for storage resources, such as S3 buckets, to restrict access to authorized users and applications. Use IAM policies and VPC endpoints to control access from within your VPC.
Audit Storage Access Logs: Regularly audit storage access logs to identify and investigate suspicious activity. This can help detect unauthorized access attempts or data exfiltration.
Step 3: Secure Your Networks
Use VPCs and Subnets: Create virtual private clouds (VPCs) to isolate your resources from the public internet and control network traffic. Divide VPCs into subnets based on security requirements.
Implement Network Access Control Lists (NACLs): Utilize NACLs to define rules for incoming and outgoing network traffic at the subnet level. NACLs provide an additional layer of security beyond VPCs.
Use Security Groups: Employ security groups to control inbound and outbound traffic at the instance level. Security groups allow or deny traffic based on specified rules, providing granular control over instance access.
Monitor Network Traffic: Continuously monitor network traffic for suspicious activity, such as unusual traffic patterns or attempts to access unauthorized resources. Use tools like VPC Flow Logs and CloudWatch Logs for monitoring.
Step 4: Secure Your Applications
Implement Web Application Firewalls (WAFs): Utilize WAFs to protect web applications from common attacks, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Regularly Patch and Update Software: Keep your applications, operating systems, and middleware up to date with the latest security patches to address newly discovered vulnerabilities.
Scan for Vulnerabilities: Regularly scan your applications and systems for vulnerabilities using automated tools. Promptly address identified vulnerabilities to prevent exploitation.
Implement Secure Coding Practices: Follow secure coding practices to avoid introducing vulnerabilities into your applications. Use secure libraries, validation techniques, and input sanitization.
Step 5: Monitor and Audit Your AWS Account
Enable CloudTrail: Activate CloudTrail to log all actions performed within your AWS account. This provides a record of activity for auditing and investigation purposes.
Configure CloudWatch Alarms: Set up CloudWatch alarms to alert you when specific events occur, such as failed login attempts, resource usage spikes, or security policy changes.
Regularly Review Logs and Audit Trails: Periodically review logs and audit trails to identify potential security breaches, unauthorized access, or misconfigurations.
Conduct Security Assessments: Regularly conduct comprehensive security assessments of your AWS environment to identify and address potential risks.
WARNING
Remember, cloud security is an ongoing process that requires continuous attention and adaptation. By implementing robust security measures, staying informed about emerging threats, and seeking expert guidance when needed, you can effectively protect your cloud resources and maintain a secure cloud environment.
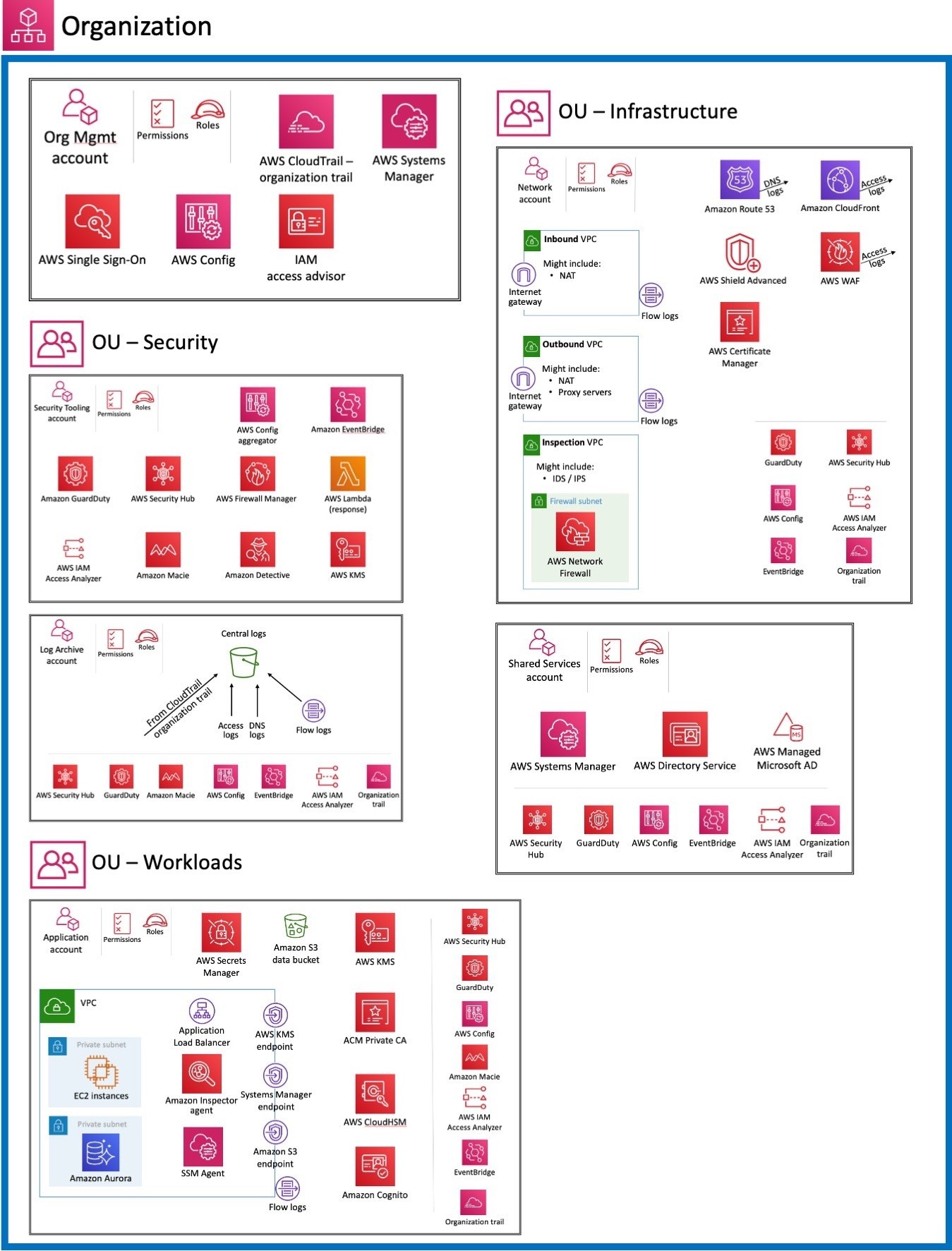
Security Reference Architecture